Connecting AWS to GCP
**DISCLAMER - To get this setup working you will need paid account for both AWS and Google Cloud Platform. Fees do apply for both AWS and GCP
Connecting a AWS VPC to Google’s Cloud Platform over VPN is pretty straight forward compared to connecting a AWS Region to Region.
To get started you will need to sign up for a Google account. From there you can log into the Google Developer Console (http://console.developers.google.com).
From here you have to create what Google calls a project. A project encapsulates most of the Google Cloud products. You can have multiple projects in your account. A project in GCP can be compared to a VPC in AWS, but there is not a complete 1 to 1 mapping with products and features. A project offers a degree of logical separation, authentication and billing to your GCP account. You can get a project setup free. For this post I am focusing in on the Networking and VPN setup. To get going with these features you have to enable billing for your project. Google does free trials in the form of starter credits. This will give you 300$ to use up in 90 days https://cloud.google.com/free-trial/.
Quick Start - Using Static Routing
- Start with GCP create a Google Compute Engine VPN gateway.
- Give your Google Compute Engine VPN a name.
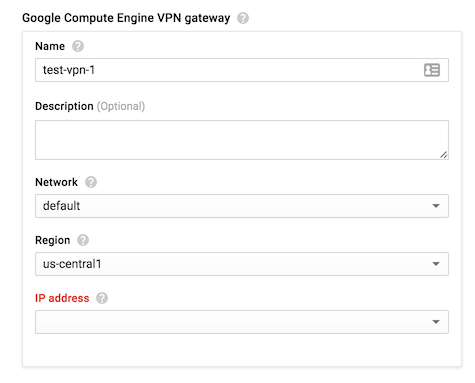
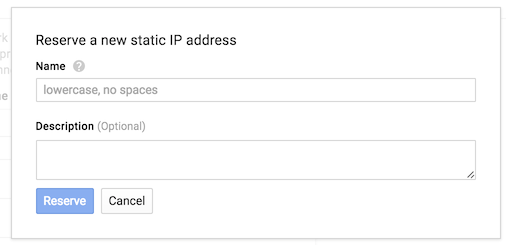
- Select a Network, Region and IP Address. If you do not already have a IP address select New Static IP Address.
- Go to the AWS VPC Dashboard.
- Create a new Customer Gateway using the Google Compute Engine Static IP address you just created.
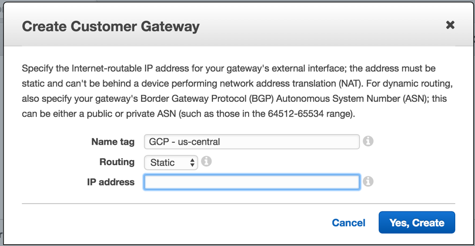
- Go the AWS VPN Dashboard
- Create a new VPN Connection using the AWS Customer Gateway (CGW) you just create. Select Static for the Routing Option. Then enter the subnet for your Google Computer Engine Network.
- Click Yes Create and you VPN will start to build on the AWS Side.
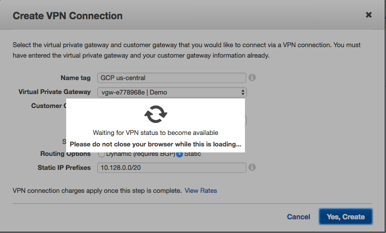
- Once the AWS VPN tunnel is built you can select the newly built VPN connection and download the Generic VPN configuration.
- This should download as a text file named with the AWS VPN ID.
- In this configuration file you will need the AWS endpoints and PSKs
- Back in the GCP console, under tunnels
- The Remote peer IP address will be the Virtual Private Gateway from the AWS VPN configuration.
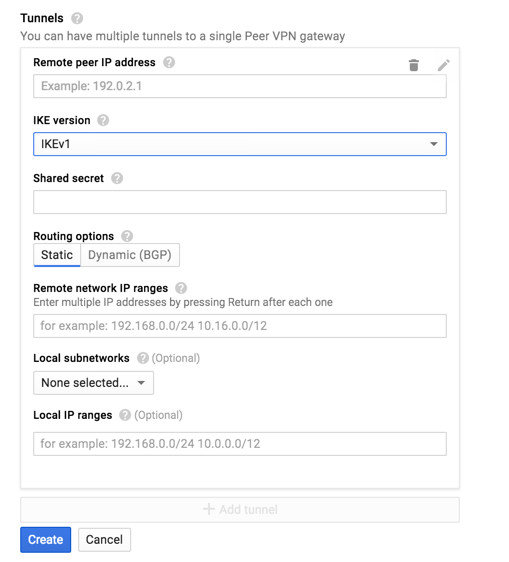
- The Shared secret is the PSK from the AWS VPN configuration
- Select IKEv1 for the IKE version
- For Remote network IP ranges enter the CIDR range of your VPC subnet in AWS
- For local subnet network add select your GCP network that you want to connect to.
- Click Create
- Now follow these steps again for the second tunnel that AWS provides the AWS VPN configuration.
- Once you click Create Google Cloud Platform will start building the tunnel and attempt to connect to the AWS Remote peer IP address.
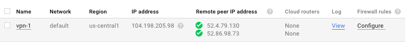
- AWS does not provide any log to help troubleshoot connection issues, fortunately GCP does.
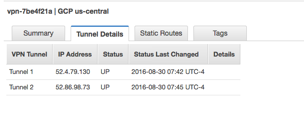
- To troubleshoot issues with AWS to GCP tunnel click on logging in the GCP VPN dashboard. This will take you to the Logging dashboard with a real time output of logs from the VPN tunnel.